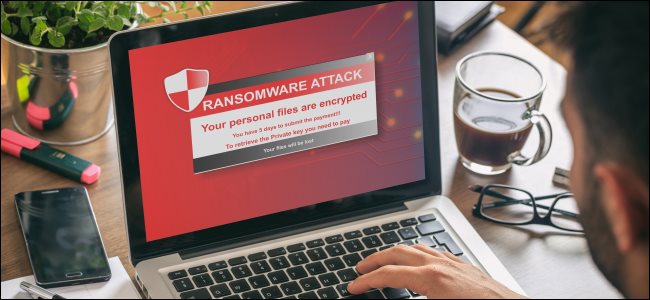
How to Protect Your Mac From Ransomware

How to Protect Your Mac From Ransomware? macOS has a relatively good reputation for security as a result of Apple’s tight grip, but no platform is safe from attack. Ransomware is just one example of this, and it’s a growing problem. Here’s how to keep your Mac safe.
Understanding What Ransomware Does
As the name suggests, ransomware takes your computer, or the information stored on it, hostage and demands a ransom for its safe return. Some particularly early Windows ransomware was known to restrict access to your machine entirely. However, a more common approach is to encrypt your data with a key that you don’t know.
With your machine or data held hostage, demands are then made for payment to restore access. This ransom might be cash sent via a wire service, like PayPal or Western Union, or gift card codes for services like Xbox Live, or even Bitcoin or other untraceable cryptocurrencies.
While ransomware might restore access to your computer or data once you’ve paid up, there’s no guarantee. Some ransomware has been known to delete data entirely, making retrieval impossible. That’s why it’s a bad idea to ever engage with a scam like this.
Unfortunately, many people are embarrassed they were set up in the first place, which makes playing along with the scam even more tempting. The nefarious ways in which ransomware spreads makes it even more likely the victim will pay to save face.
Fortunately, there are some ways you can protect yourself. The same as many other online scams, the best thing you can do is avoid activities that put you at risk in the first place.
RELATED: Microphone Not Working on a Mac? Here’s How to Fix It
Avoid Pirated Software
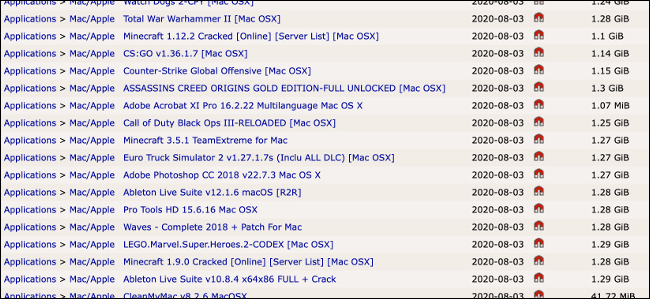
One of the primary vectors for spreading ransomware is pirated software. In June 2020, Malwarebytes discovered the ransomware “ThiefQuest” (originally dubbed “EvilQuest”) hiding in an installer for a cracked version of Little Snitch. There were also suggestions that the malware had made its way into pirated versions of DJ software, like Ableton Live and Mixed in Key 8.
These installers spread via BitTorrent after originally being posted to a Russian forum dedicated to sharing cracked software. These torrents are shared far and wide, and tracked by “mainstream” trackers, like The Pirate Bay. You don’t have to be combing the internet for questionable forums to stumble across some potentially infected installers.
Since pirates often modify installation files or include additional patches designed to crack the apps in question, piracy poses a very real threat of infecting your computer with malware. Even if a torrent appears to be legitimate or is released by a group you’re familiar with, you never know what you’re downloading.
Also, be wary of software passed around by friends or acquaintances if you don’t know the source. While it can be tempting to install expensive software for free, it could cost you a lot more than the price of a license.
We recommend you seek out alternatives that are cheaper, or go for open-source software. You might even want to give a Netflix-esque solution like SetApp a try.
Be Careful Online
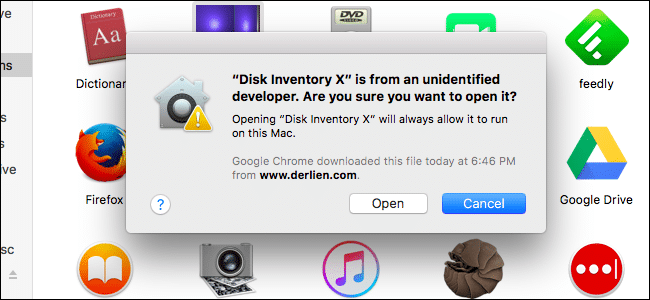
It’s not just pirated software that spreads malware. Just about any executable file could be a threat, so it’s a good idea to use common sense whenever you download and install software. This is one of the reasons Apple introduced Gatekeeper, which favors the Mac App Store and signed apps from certified Apple Developers.
When you try to install an application that breaks these rules, Gatekeeper will tell you the app couldn’t be installed because it’s not from an identified developer. You can choose to ignore this (under System Preferences > Security and Privacy). However, you then assume any risk involved in running software that could have come from anywhere.
It’s important to note, though, that the vast majority of unsigned software isn’t malicious. For an app to become Gatekeeper compliant, the creator must register as an Apple developer and pay $99 per year. As a result, many legitimate projects remain unsigned due to budgetary constraints. This is particularly true of open-source projects, which rely on voluntary programmers who only contribute their time.
If you trust a developer, then you can use an MD5 hash to check the legitimacy of a file. Most developers include an alphanumeric, cryptographic hash alongside a download link. If the hash of the file you downloaded matches the one supplied by the developer, you’ll know no one has tampered with the file.
It’s also true that although all apps in the Mac App Store are Gatekeeper-friendly, malware has appeared in both iOS and the App Store in the past. Generally, though, because software in the App Store is subjected to a higher level of scrutiny, it’s safer.
Have a Solid Backup Plan
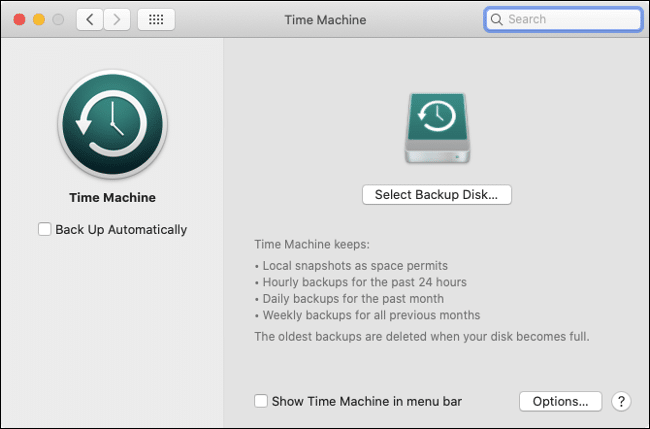
Backups are important. In an ideal world, you should back up locally to an external drive via Time Machine. There should also be a remote internet back up in place in case a fire or other event destroys both your computer and Time Machine drive.
When it comes to ransomware, backups are even more vital. There are a few rules to follow, though. First, you should disconnect your Time Machine backup when it’s not in use. Before macOS Catalina, software could access all but the most sensitive parts of your system drive, including any connected external drives.
While Catalina walks back most of that, it’s still possible for attackers to circumvent such protections. We’ve seen examples in the past of malware bypassing Gatekeeper and circumventing System Integrity Protection.
Always assume the worst and disconnect your Time Machine drive when your backup is complete.
Better still, avoid installing software or updates while a backup is taking place. If your backup drive is permanently connected over the network or via some sort of storage array, you can unmount it when it’s not in use. Right-click it on your desktop, and then choose “Unmount.”
If your Mac becomes infected and you have a backup ready to go, you can nuke everything, reinstall macOS, and restore all of your personal files. However, if your Mac is infected and your backup drive is mounted, your backup drive could be held hostage, too. If you’re using a version of macOS that’s older than Catalina, this risk is elevated.
Again, a cloud-based backup solution could be your savior in this scenario. Just be sure to pick a provider that includes versioning, so you can roll back to any unencrypted versions of your files if the unthinkable occurs.
Consider Anti-Malware Software
We’ve said it before and we’ll say it again: you don’t really need antivirus software for your Mac. “Hand-holding” technologies, like Gatekeeper and System Integrity Protection, are there to protect your computer. Apple’s invisible malware scanner, XProtect, also runs constantly in the background, scrutinizing everything you do.
That’s not to say that anti-malware tools don’t have their place on macOS. Many people feel more comfortable knowing there’s an extra layer of security on their system. Some of these apps can help you identify potential threats so you can avoid them.
For basic malware removal, consider Malwarebytes (we like the Windows version, too). The free version will help you remove known nasties, while the paid version (which you probably don’t need) offers real-time protection.
We haven’t independently tested the rest of the field, but AV-Test highly recommends the following as of June 2020:
- Avira Antivirus Pro
- Bitdefender Antivirus for Mac
- ClamXAV
- F-Secure SAFE
- Kaspersky Cyber Security
- Norton Antivirus
- Trend Micro Antivirus
Are you concerned about ransomware and other threats to your Mac? Brush up on the basics of online security to keep viruses, hackers, and thieves at bay.







Leave a reply